NY SHIELD: Maintaining Data Security Safeguards

If your company handles personal data or private information belonging to a New York resident, then you must comply with the data security obligations set out in the Stop Hacks and Improve Electronic Data Security Act (SHIELD). You must:
- Demonstrate your commitment to improving cybersecurity by setting up a data security program
- Implement safeguards throughout your organization for protecting data (known as implementing "reasonable safeguards")
- Notify individuals if there's a data breach, without undue delay
If you fail to comply with the terms of the SHIELD Act, you risk serious financial consequences including pecuniary fines and reputation damage.
So, what's the point of the Act, and how do you comply with your obligation to safeguard data? We'll show you what you need to do and explain why.
Need a Privacy Policy? Our Privacy Policy Generator will help you create a custom policy that you can use on your website and mobile app. Just follow these few easy steps:
- Click on "Start creating your Privacy Policy" on our website.
- Select the platforms where your Privacy Policy will be used and go to the next step.
- Add information about your business: your website and/or app.
- Select the country:
- Answer the questions from our wizard relating to what type of information you collect from your users.
-
Enter your email address where you'd like your Privacy Policy sent and click "Generate".
And you're done! Now you can copy or link to your hosted Privacy Policy.
- 1. NY SHIELD Act: What You Need to Know
- 2. What is Personal Information?
- 3. What is Private Information?
- 3.1. Data Not Covered Under the SHIELD Act
- 4. Who Does the SHIELD Act Apply to?
- 5. SHIELD Act Compliance Requirements
- 5.1. The SHIELD Act Data Breach Notification Requirement
- 6. Data Safeguarding: Your Responsibilities
- 6.1. The Physical Safeguards
- 6.1.1. Risk Assessment
- 6.1.2. Intrusion Detection
- 6.1.3. Data Protection
- 6.2. The Technical Safeguards
- 6.2.1. Design Risk Assessment
- 6.2.2. Transfer and Storage Risk Assessment
- 6.2.3. Malfunction Detection
- 6.2.4. Testing and Monitoring
- 6.3. The Administrative Safeguards
- 6.3.1. Employee Responsibility and Education
- 6.3.2. Managed Service Providers (MSPs)
- 7. Conclusion
NY SHIELD Act: What You Need to Know
New York's Stop Hacks and Improve Electronic Data Security Act protects the personal information that people share online. It aims to:
- Enforce strong data privacy and cybersecurity
- Make companies notify users if their data is compromised
- Make companies proactively mitigate risks for data breaches
The SHIELD Act safeguards personal and private information.
What is Personal Information?
Personal information is defined in the Act as any information which can identify a natural person:
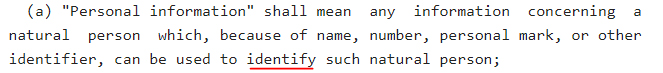
Examples of personal information include someone's name, or their home address.
What is Private Information?
Private information is divided into three categories: category I, category II, and category III.
Category I private information is the combination of any personal data and what's known as a data element. The data element must either be unencrypted or encrypted but compromised.
The specific data elements are:
- Social Security Numbers
- Driver License Numbers or Non-driver ID card number
- Account number, credit card number, or other financial account number if the access codes are also available (i.e., if it's possible to access the account)
- Biodata
So, information is private if it's either easily used to identify someone, e.g. their name, or it's potentially used to identify someone and it's unencrypted or compromised.
For example, a combination of a full name and unencrypted credit card number is category I private information. It's personal information if it's a full name but the card number is encrypted and uncompromised. For clarity, here's what the Act says:
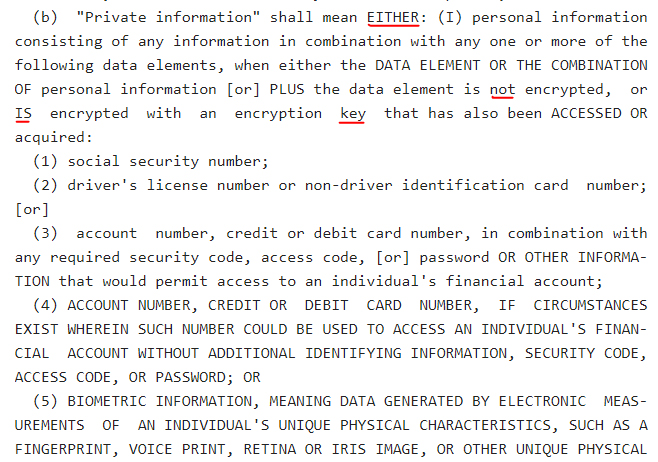
Category II private information is an email address or username that's accessible to unauthorized users because the password and/or access code is available. Category III private information is healthcare data.
Data Not Covered Under the SHIELD Act
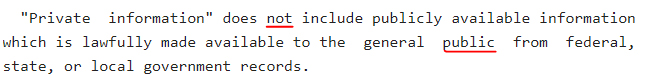
Just because data can identify someone doesn't automatically mean it's personal or private data protected by the SHIELD Act. If the information is lawfully available to the public, such as census data, it's not covered by the Act:
Now we're clear on the data covered by the Act, let's consider who must comply with the Act and, more specifically, the steps that relevant organizations must take to safeguard data.
Who Does the SHIELD Act Apply to?

Essentially, if you hold, own, or license personal or private information belonging to New York residents, you're covered by the Act. It's irrelevant whether your company is based in New York, and it doesn't matter why you hold the data (unless it's an exempt category such as referred to above). It only matters that you hold the data in the first place.
So, if you possess or handle data belonging to a New York resident, you're responsible for:
- Keeping it safe
- Mitigating the risks of cyber attacks
- Proactively tackling data breaches
- Notifying breach-affected individuals as soon as possible
If there's a chance your website is accessed by New York residents, you must abide by the terms of the SHIELD Act. Let's briefly consider your obligations before diving into data safeguarding in more detail.
SHIELD Act Compliance Requirements

Chances are, if you're complying with other major privacy laws including the California Consumer Privacy Act (CCPA) and the General Data Protection Regulation (GDPR), you're probably complying with the SHIELD Act. However, let's be clear on the specific obligations placed upon your company under the SHIELD Act.
Compliance comes down to two main criteria. You must:
- Notify users of a data breach if there's reason to believe that the data has been unlawfully acquired or accessed e.g. by unauthorized persons
- Implement safeguards that are reasonably robust enough to protect personal and private information belonging to New York residents
The SHIELD Act Data Breach Notification Requirement
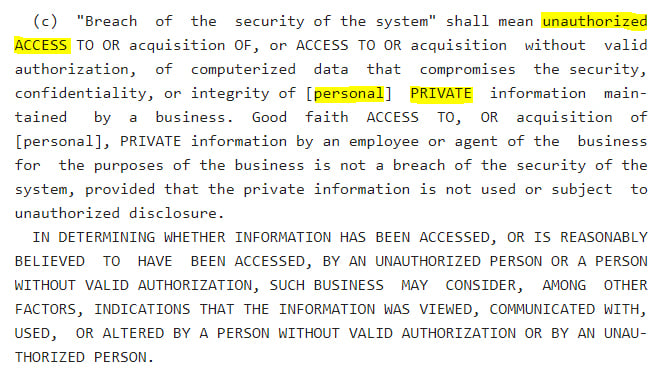
One of the most significant components of the Stop Hacks and Improve Electronic Security Act is the data breach notification requirement. You're obliged to report a data breach to a New York resident if:
- You hold their private information; and
- You have a reasonable belief that someone accessed or acquired this data without authorization, and this access compromises data security
If you suspect that someone has accessed private data without authorization, you're obliged to inform the affected individual expediently, i.e. without unreasonable delay. The Act doesn't specify a time limit here. What's reasonable varies from situation to situation.
There are some caveats to this. You don't need to notify users about a potential data breach if:
- An authorized person accessed the data
- They accidentally disclosed this information
- The business reasonably believes that the disclosure won't result in financial harm, emotional harm, or data abuse
In most cases, you need to tell New York residents about a possible data breach. You don't need to inform them if an authorized person accessed the data and accidentally disclosed it in good faith and damage is unlikely.
Data Safeguarding: Your Responsibilities

You must take steps that are reasonable in the circumstances to protect, erase, and dispose of personal data. What's reasonable varies depending on, for example, the size of your business, the type of data you're handling, and your sector compliance requirements.
There are three main categories of safeguards:
- Physical - e.g. intrusion prevention, risk management
- Technical - e.g. network design assessment, failure detection
- Administrative - e.g. training and employee management
Safeguards should be an integral part of your overall data security program. Let's take a closer look at each category to help you implement safeguards for your own security program.
The Physical Safeguards
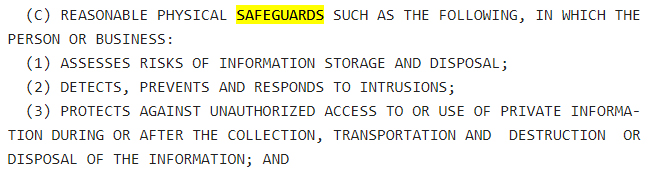
Physical safeguards are key to any data safeguarding strategy. As the Act says, you must:
- Perform a risk assessment of your data disposal and storage processes - i.e., you must understand any risks associated with these processes and take steps to mitigate them
- Have a process for detecting, responding to, and preventing malicious intrusions
- Have ways to protect data from unauthorized access during its transfer or storage
So, what are some examples of physical safeguards?
Risk Assessment
It's on you to assess your information storage and disposal processes and show that you've taken reasonable steps to mitigate and reduce risk of unauthorized access.
Examples of risk assessment include:
- Understanding how data moves around your organization
- Ensuring data is encrypted or otherwise secured
- Deleting all traces of data upon its disposal
- Physically securing hardcopy backup storage areas
- Securing digital data through encryption or other tools
Never keep data for longer than necessary. The longer data is in your possession, the more likely it is that it'll be hacked or accessed. Change passwords regularly, and always use password protection or encryption for files kept on remote platforms such as the cloud.
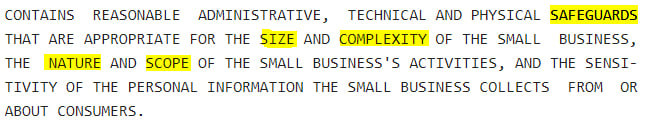
The Stop Hacks and Improve Electronic Security Act doesn't tell you what physical safeguards to employ - it all comes down to the size of your business and the type of data you're handling:
Intrusion Detection
Every company needs reliable intrusion detection mechanisms. You must decide what level of intrusion detection is proportionate for your business.
The goal of intrusion detection is simple - detecting malware, phishing scams, and other malicious activity before it can infiltrate your systems. Intrusion detection includes:
- Firewalls and anti-virus software
- Network monitoring and remote surveillance
- A software-based detection system
- CCTV for monitoring unauthorized physical access
Remember that safeguards aren't just defense tools. They're proactive and designed to spot problems before they arise. Keep anti-virus software, detection software, and firewalls up to date, and remotely monitor your premises at all times.
Data Protection
Data must be protected at every stage if it's in your possession. This includes right up until you've safely disposed of it. Examples of data protection safeguards include:
- Password protection and encryption
- Locking physical files and hard copies away somewhere safe
- Limiting access to authorized users only
- Only holding however much data you need for business purposes
- Use software tools to safely erase data
Every industry has sector-specific compliance requirements. Familiarize yourself with these. And, if you're complying with the data protection requirements enforced by GDPR, CCPA, etc., then you're probably already complying with this safeguarding obligation.
The Technical Safeguards

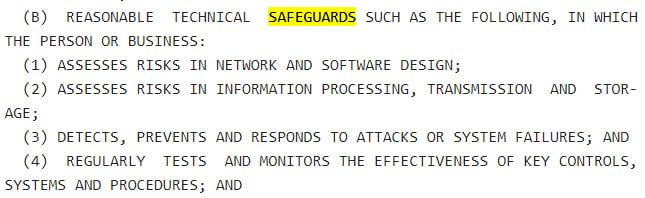
Technical safeguards are more specific than physical safeguards. The safeguards all come down to risk assessment and mitigation. The Act sets out that you must:
- Assess network and software risks
- Assess storage and data transmission risks
- Take steps to detect and remedy system malfunctions
- Audit and monitor your processes for effectiveness
Here is the clause in detail:
How, then, do these technical safeguards work?
Design Risk Assessment
You must ensure that your network and software are securely designed.
- Always have up-to-date router firmware in place.
- Install an intrusion detection system (IDS) to spot threats before they infiltrate.
- Make use of wi-fi protected access (WPA). This allows you to password protect your router so your network is secure at an infrastructure level.
- Develop a network security policy. This security policy sets out the identified risks and how you plan on managing those risks.
It's impossible to eliminate all risk. What matters is that you take reasonable steps to reduce risks to an acceptable level. The cost of implementing a secure network and infrastructure should never exceed the likely cost of a data breach.
Always remember to expand your network security to cover any new hardware such as PCs when they're introduced into the company.
Transfer and Storage Risk Assessment
Information should be safely and securely transferred and stored. Here are some examples of measures to take:
- Use a virtual private network (VPN). A VPN allows you to encrypt your internet connections and better secure the data transferred around your network.
- Disable file sharing.
- Use secure sockets layer (SSL) certificates for secure transactions.
- Only allow authorized personnel access to sensitive data.
Encrypt data wherever it's stored, whether it's on a disk or in the cloud. Delete old data as soon as possible, and keep secure backups.
Malfunction Detection
Your data security program only works if you can respond to threats and system malfunctions expediently. Here are some suggestions:
- Have processes in place for quickly blocking bad source IPs from accessing your network.
- Separate public and private wireless networks in your business. If hackers access or corrupt the public access, they can't corrupt the private one if they can't access it.
- Draft a disaster management plan based on how you'll respond to incidents at all levels, from minor computer crashes to catastrophic natural disasters.
Testing and Monitoring
Don't wait until disaster strikes to test your safety designs. Here are some tips for establishing testing and monitoring safeguards:
- Frequently audit your threat detection and response times.
- Simulate a cyberattack using penetration testing and address any weaknesses in your organization's response.
The Administrative Safeguards

Every organization must put reasonable administrative safeguards in place for day-to-day data security management. According to the Act, you should:
- Appoint at least one employee as a security officer
- Conduct regular risk assessments
- Assess your existing processes at regular intervals
- Employ service providers to help with IT needs

We've already covered much of how to protect your network, software, and infrastructure, but let's cover one or two remaining points.
Employee Responsibility and Education
It's your responsibility to ensure your staff receive regular training and knowledge updates on cybersecurity matters. Here are some tips:
- Enforce good password practices including creating strong passwords, keeping them safe, and changing them regularly.
- Ensure staff know who to approach with security concerns. Appoint a security officer.
- Limit the employees with access to sensitive data.
- Educate employees on common security scams including phishing emails and telephone calls.
Again, you only need to take reasonable measures that are proportionate to your business.
Managed Service Providers (MSPs)
MSPs allow you to outsource your cybersecurity and compliance needs to an external provider with the latest hardware, software, and network security. They're recommended by the Act because they're a "one stop shop" for your security needs, and they allow you to focus on growing your business without worrying about data privacy.
These firms can support you with everything from industry compliance requirements to disaster planning, and for firms in high-risk industries such as healthcare and finance, they are an invaluable, cost-effective security solution. They typically work on a flat fee model so you only pay for the services you need, and you can always expand your contract with them as your business grows.
For medium to large-sized businesses, MSPs are certainly a proportionate answer to all your security-related problems.
Conclusion
The Stop Hacks and Improve Electronic Data Security (SHIELD) Act protects private and personal information belonging to New York residents. All businesses that store, collect, transfer, or lease personal data belonging to a New York resident must comply with its terms.
Essentially, you must:
- Draft and implement a data security program
- Tell affected individuals if there's been unauthorized access to their personal information
- Implement reasonable safeguards to keep personal data secure
There are three categories of safeguards - physical, technical, and administrative - and every business must adopt at least some safeguards applicable to each category. You only need to take reasonable steps to mitigate risk of unauthorized access to data. It's not necessary, or possible, to eliminate all risks, but you do need to make appropriate efforts to stay in compliance.