India IT Act 2000

If you have commercial operations in India, then you need to comply with India's Information Technology Act 2000 ("IT Act"). The IT Act covers a variety of cybercrime and privacy issues, and the penalties for violating the Act are among the strictest in the world.
Below, we consider how the IT Act works, who must comply with it, and how you can ensure legal compliance within your business.
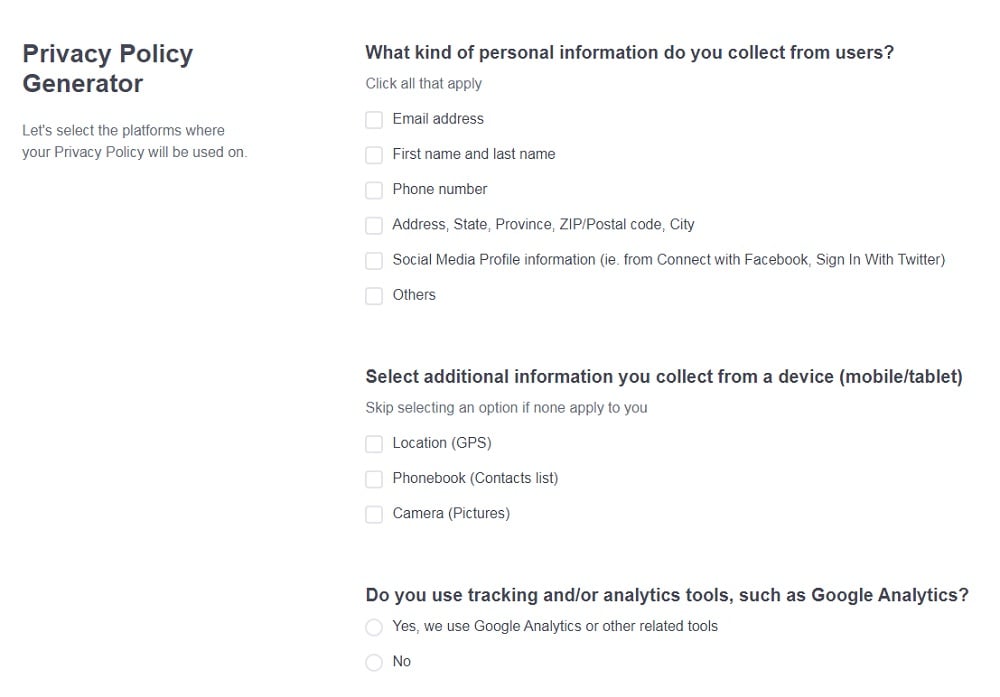
Need a Privacy Policy? Our Privacy Policy Generator will help you create a custom policy that you can use on your website and mobile app. Just follow these few easy steps:
- Click on "Start creating your Privacy Policy" on our website.
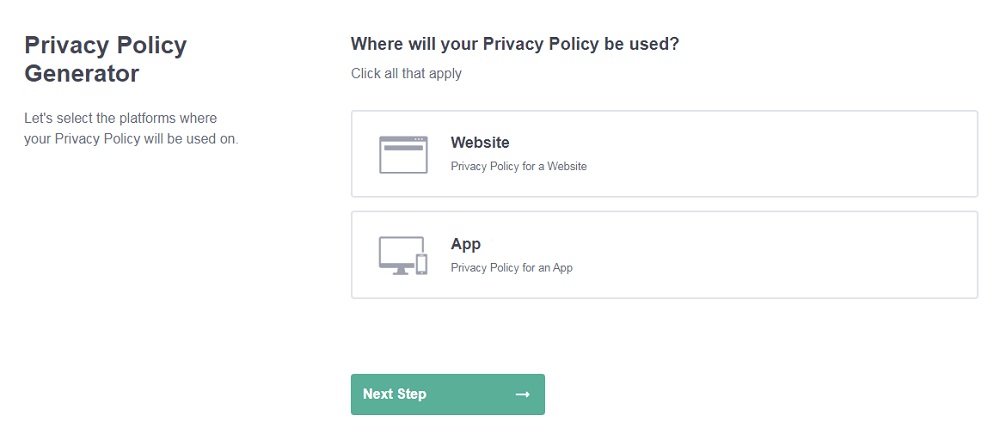
- Select the platforms where your Privacy Policy will be used and go to the next step.
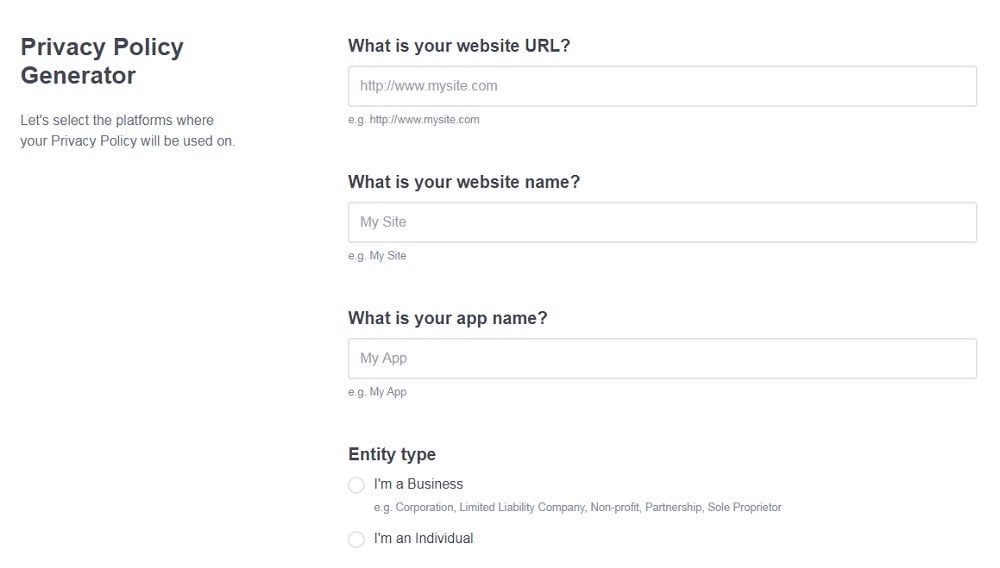
- Add information about your business: your website and/or app.
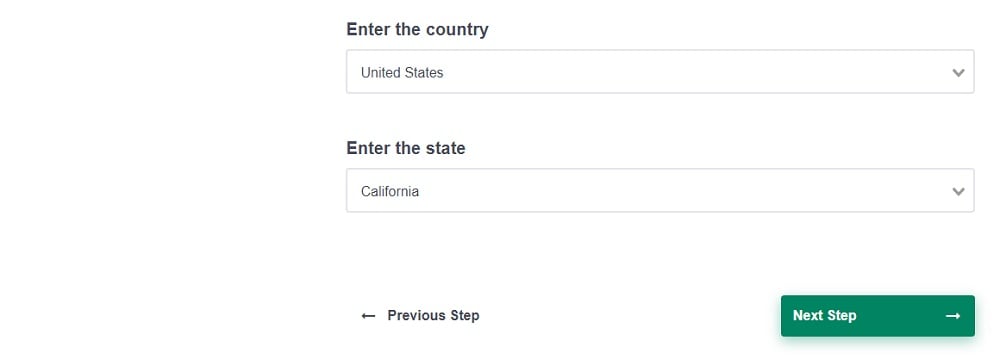
- Select the country:
- Answer the questions from our wizard relating to what type of information you collect from your users.
-
Enter your email address where you'd like your Privacy Policy sent and click "Generate".
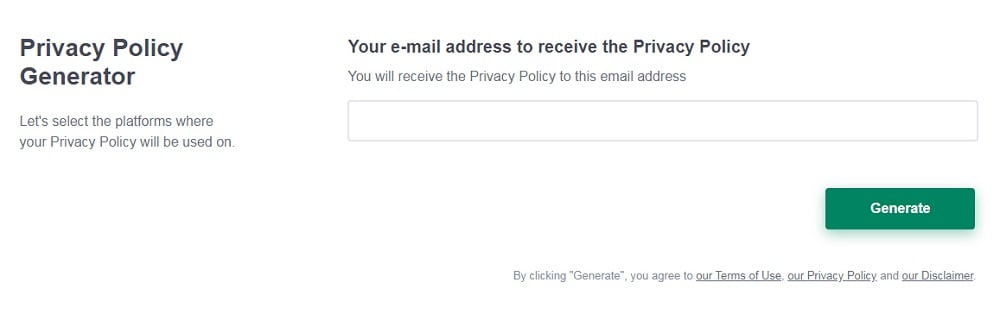
And you're done! Now you can copy or link to your hosted Privacy Policy.
- 1. What is the IT Act?
- 2. Main Purposes of the India IT Act 2000
- 3. Who Does the India IT Act 2000 Apply to?
- 4. Right to Sue Under the India IT Act 2000
- 5. Offenses Under the India IT Act 2000
- 5.1. Acquiring Stolen Computer Devices
- 5.2. Computer System Hacking
- 5.3. Cyber Terrorism
- 5.4. Failure to Comply With Government Decryption Requests
- 5.5. Failure to Keep Records
- 5.6. Hacking Protected Systems
- 5.7. Misrepresentation
- 5.8. Online Cheating Scams
- 5.9. Source Code Tampering
- 5.10. Unauthorized Password Use
- 5.11. Unauthorized Transmission of Lewd Information
- 6. Complying With the India IT Act 2000
- 6.1. 1. Get Express Consent
- 6.2. 2. Check Where Servers are Located
- 6.3. 3. Control User Generated Content (UGC)
- 6.4. 4. Implement a "Privacy by Design" Framework
- 7. Penalties for Non-Compliance with the India IT Act 2000
- 8. India IT Act 2000: Key Takeaways
What is the IT Act?
The IT Act is a cybercrime law. For example, it makes the following acts legally punishable:
- Hacking
- Source code tampering
- Identity theft
- Virus or malware circulation
Using computers to distribute lewd content or facilitate terrorism are also crimes under this act.
At its heart, the IT Act is also a communication law. It regulates IT offenses committed by businesses via "electronic commerce" and electronic communication. It covers all mediums of e-communication, including email and messaging platforms.
For example, crimes committed by email or by instant messaging could be covered by the IT Act.
There are civil and criminal punishments for breaking the IT Act, depending on the violation. For example, you might incur a civil fine or you could face jail for a criminal charge. We'll cover the penalties in detail below.
Main Purposes of the India IT Act 2000

The IT Act serves three main purposes:
- To protect citizens from identity theft and related cyber crimes
- To support ecommerce by regulating the use of electronic signatures
- To control and protect information exchanged electronically
In simple terms, the IT Act regulates electronic communications and makes ecommerce safer and more secure. It gives citizens more control over what happens to their personal data and how it's shared, and it gives them rights if they're a victim of cybercrime.
Who Does the India IT Act 2000 Apply to?

The rules around who must comply with the IT Act are somewhat confusing at first glance. In general terms, though, you must comply with the IT Act if you physically operate in India. Meaning, you do business in India.
You don't need to comply if you just have customers based in India. It's only if you have a physical or tangible presence in the country that you're bound by the IT Act.
A physical presence can mean having an office based in India. Examples of companies with offices in India are Amazon, American Express, and Google.
However, it can also mean simply having an electronic presence e.g. having servers based in India. If you outsource to India or have any entities registered in the country, then you have a presence there.
For example, if you run a social media platform with Indian users, but you have no ties electronically or physically to India, you are not bound by the IT Act. But if you have servers there, you are.
Right to Sue Under the India IT Act 2000
The IT Act makes it possible for private citizens to sue for cybercrime. For example, if they've been hacked, they can make a civil claim under Section 46 of the Act. If an experienced adjudicator agrees that they have a claim, they may award them compensation.
There's also the possibility that the wrongdoer will face criminal charges, depending on the incident.
Offenses Under the India IT Act 2000

The IT Act criminalizes many types of actions. It's one of the most comprehensive laws of its kind in the world. The offenses are listed in Chapter XI "Offenses." Here is an outline of the main offenses.
Acquiring Stolen Computer Devices
Under Section 66B, it's an offense to receive or retain a "computer resource" or device if you have reason to suspect that it's stolen. A computer resource is defined in section 2(k) as any computer, database, network, or software, so it applies to most communication devices.
Violating this clause incurs penalties of up to three years' imprisonment or a fine of 100,000 rupees.
Computer System Hacking
Section 66 makes it an offense to hack a computer system. Charges may be brought under this clause if you deliberately access, delete, or damage information, knowing that you may cause loss or damage.
The penalty is up to three years' imprisonment and/or a fine.
Cyber Terrorism
Cyber terrorism is an act that threatens India's sovereignty or the public (Section 66F). Knowingly using a computer or system to commit acts of terror means facing up to life in prison.
Failure to Comply With Government Decryption Requests
The government may request that you take certain actions, like sending them decrypted information, if it's in the public interest. A failure to comply means you face up to seven years in prison.
Failing to comply with any official request to stop certain activities could incur a fine of up to two lakh rupees and/or three years in jail.
Failure to Keep Records
Businesses and intermediaries must keep electronic records for certain periods of time determined by the government. This is for auditing and security purposes and to help law enforcement agencies perform their own duties.
A failure to maintain these records could result in a fine or up to three years in jail (Section 67C).
Hacking Protected Systems
Although the IT Act prohibits hacking the public, hacking or illegally accessing a government system is a separate offense. Only those with express government permission can access these networks and computer systems. The details are published in India's Official Gazette.
You could be jailed for up to 10 years for accessing or attempting to access a protected system (Section 70).
Misrepresentation
It's an offense to conceal or misrepresent facts to the government or its official agencies (Section 71). You could be fined up to one lakh rupees and/or be jailed for up to two years for misrepresentation.
Online Cheating Scams
You can't use computer systems to cheat or scam the public by, for example, posing as a legitimate business. Any form of online impersonation for financial gain could lead to three years in jail or one lakh rupees in fines (Section 66D).
Source Code Tampering
Computer source code is any computer command, design, or layout for a program (Section 65). Tampering with computer source code, or concealing or destroying it, could mean a fine of up to two lakh rupees and/or three years' imprisonment.
Unauthorized Password Use
The IT Act takes identity theft and impersonation seriously. Using someone else's password, e-signature, or other online identifiers e.g. login details could be jailed for three years or made to pay up to one lakh rupees in fines.
Unauthorized Transmission of Lewd Information
It's an offense to transmit or publish obscene and lewd content under the IT Act Section 67. This extends to content which is intended to corrupt or deprave the likely audience. This clause covers a potentially huge range of content, and the penalties are severe: up to 10 years' imprisonment and two lakh rupees in fines.
Seek legal advice if you're unsure how to comply with this section as it is significantly broad.
Complying With the India IT Act 2000

Unfortunately, the IT Act does not provide much specific information to help us understand how to comply with its provisions. However, there are four general steps you should take to ensure IT Act compliance.
1. Get Express Consent
Under the IT Act's subsidiary legislation, the IT Rules 2011, businesses need consent to collect and share "sensitive personal data or information" (SPDI). This is essentially any data which can be used to identify someone and includes:
- Email addresses
- Passwords
- Financial data
- Biometric data
You don't need consent if your contract with the individual provides for the disclosure of SDPI, or if you need to disclose it to comply with other legal obligations. In most cases, however, you do need consent.
This consent must be in writing to be valid. Typically this means the individual must give express consent by letter or email. This is a significant burden for businesses because it's not easy to secure such consent. However, it's essential unless:
- Your contract with the individual expressly provides for disclosing SDPI, or
- The information you have is freely available or in the public domain
Get legal advice if you're unsure whether you need to contact individuals to secure express consent.
2. Check Where Servers are Located
If you outsource to India, or your servers are located in India, then you must comply with the IT Act.
- Consult with your IT services provider or MSP. Check if they use servers in India.
- If they do, then you must ensure all content transmitted across these servers is compliant.
You may determine that it's best to host your content elsewhere or use different servers, depending on your business.
Remember, the IT Act applies to intermediaries, not just your business. Get confirmation, in writing, of where your servers are located so you can determine your compliance requirements.
3. Control User Generated Content (UGC)
The IT Act is one of the world's strictest online security laws. The penalties, as we'll cover below, can be significant. It's vital, then, that you find ways to limit your legal liability where possible.
One way to do this is by controlling user generated content (UGC). UGC is content that's created, distributed, or shared through your platform. If the content is, for example, obscene or criminal in nature, then you could be held liable for facilitating its distribution under the IT Act.
To control UGC, include clauses in your Terms and Conditions agreement which:
- Limit your liability for harmful content, and
- Give you the right to ban or block users who abuse your platform and violate your rules
For example, Pinterest reserves the right to ban users who violate its Terms of Service:
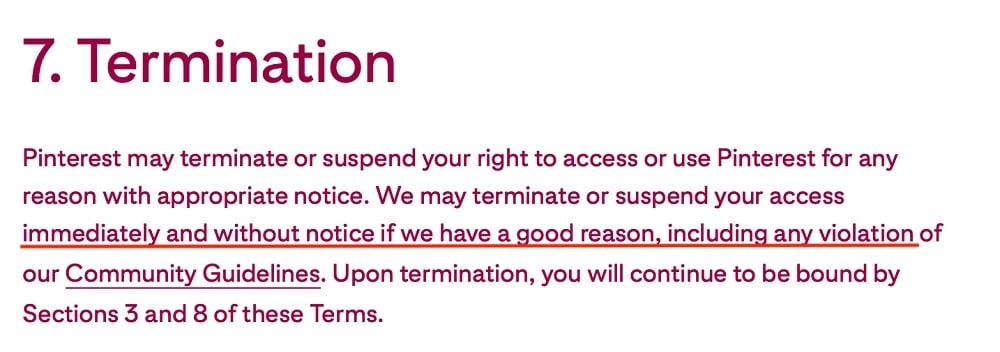
And this clause indemnifies Pinterest, or limits the company's liability, for third party actions:

Although updating your Terms and Conditions may not prevent every lawsuit, it does show your commitment to online safety which could, in turn, mitigate sanctions against you.
You can also consider using moderation procedures if feasible. Moderation lets you check content before it's posted. You can prohibit problematic content from appearing on your platform this way.
You can either use automated moderation tools or have your own staff manually moderate content before it appears online. You might use both approaches to catch as many problematic posts as possible.
4. Implement a "Privacy by Design" Framework
"Privacy by Design" (PbD) means that you've designed your IT systems around data protection. In other words, you fully considered data protection, privacy, and security concerns when designing your IT framework.
There are various steps involved in creating a PbD framework but here are some pointers to consider:
- De-identify personal data or sensitive data, where possible
- Use encryption and password protection to restrict access
- Implement firewalls and multi-layered network protection
- Map personal data so you know how it's transmitted, shared, and stored across your business
Penalties for Non-Compliance with the India IT Act 2000

If you don't comply with the IT Act, you face significant consequences. The penalties could apply directly to your business, or they may affect you as an individual.
Under the IT Act, there are two main types of penalties: financial penalties and/or imprisonment.
Compensation is payable if anyone is affected by your actions. For example, let's consider Chapter IX Section 43. If you damage someone else's computer or disrupt their service access, you may need to pay them up to one crore rupees.
The exact amount you're ordered to pay depends on, for example, whether you acted intentionally, and the value of the other person's losses.
Even if your actions don't "harm" anyone, you could still face financial penalties, and as noted above, many breaches can lead to imprisonment.
India IT Act 2000: Key Takeaways
The IT Act is one of the world's strictest cybercrime laws. It's designed to protect the public and government agencies from potentially harmful online activities. Acts criminalized by the legislation include:
- Hacking
- Online scams
- Identity theft
- Data tampering
The IT Act applies if you have any physical presence in India, whether it's an office or server located within its borders.
The penalties range from fines to significant jail time. You can ensure compliance by:
- Designing your IT systems with privacy and security in mind (Privacy by Design)
- Getting consent before capturing personal data
- Controlling UGC and terminating accounts which violate your rules
- Understanding where your servers are located and how data is stored, transmitted, and captured

