Implementing Privacy By Design
The General Data Protection Regulation (GDPR) introduced many changes to the way businesses and public bodies think about privacy. One of those ways is in the decision to encode the concept of "Privacy by Design" (PbD) into law through Article 25.
Fortunately, unlike much of the GDPR, the concept of Privacy by Design is fairly well-trodden.
What is Privacy by Design, why does the GDPR require it, and how can you implement PbD at your own business? You'll find the answers and checklists to help you along the way are below.
Need a Privacy Policy? Our Privacy Policy Generator will help you create a custom policy that you can use on your website and mobile app. Just follow these few easy steps:
- Click on "Start creating your Privacy Policy" on our website.
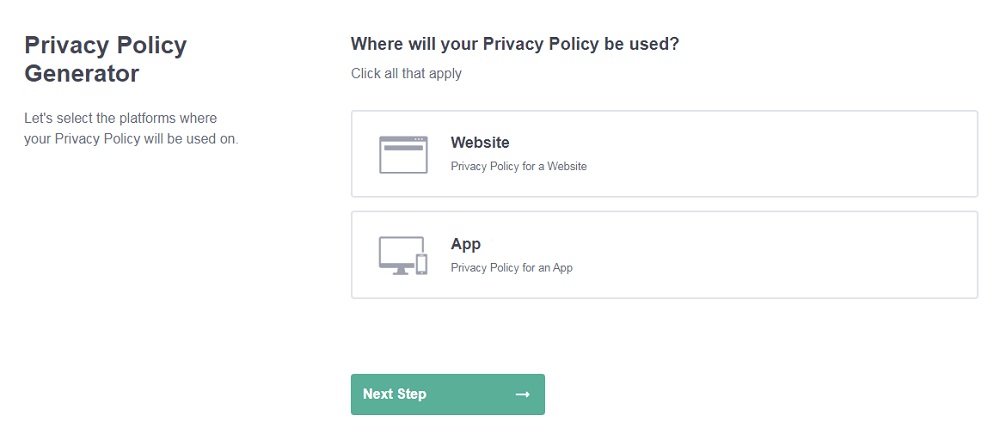
- Select the platforms where your Privacy Policy will be used and go to the next step.
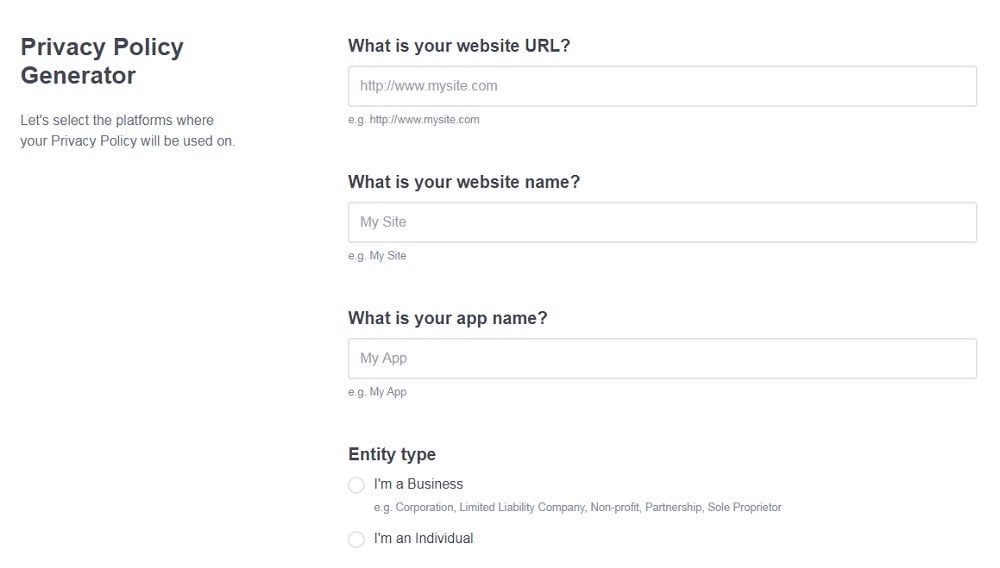
- Add information about your business: your website and/or app.
- Select the country:
- Answer the questions from our wizard relating to what type of information you collect from your users.
-
Enter your email address where you'd like your Privacy Policy sent and click "Generate".
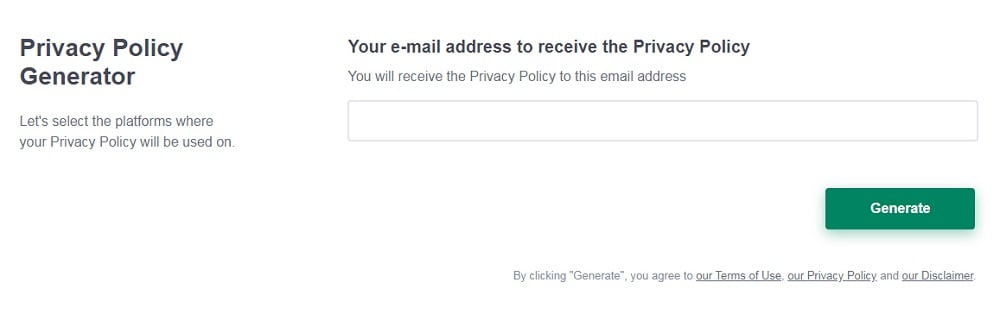
And you're done! Now you can copy or link to your hosted Privacy Policy.
- 1. What is Privacy by Design?
- 2. The 7 Principles of Privacy by Design
- 3. Privacy by Design: Who's It For?
- 3.1. What if the GDPR Doesn't Apply to My Business?
- 4. How to Implement Privacy by Design: Article 25 Checklists
- 4.1. Systems Checklist
- 4.2. Processes Checklist
- 4.3. Risk Management Checklist
- 5. Privacy by Design is a Best Practice
What is Privacy by Design?
The most basic explanation of Privacy by Design is little more than "data protection through technology design."
At its core, it means that you need to integrate data protection and privacy features into your system engineering, practices and procedures. It shouldn't be an afterthought or a supplement to your processes or infrastructure.
One way to describe it is by outlining what Privacy by Design isn't. For example, if you're an individual browsing the internet, it doesn't matter if you use a VPN and firewall to protect your computer if you also use the password: "password123" on every single account. A VPN won't make up for your use of weak passwords. You need to integrate privacy at every level and then you can add on extra security features like a VPN.
What does this mean in practice for businesses? Some examples of Privacy by Design include:
- Conducting a Data Protection Impact Assessment (DPIA) before using personal information in any way
- Providing the contact details of your Data Protection Officer (DPO) or other responsible party
- Writing a Privacy Policy that's easy to read and kept up-to-date
Even still, Privacy by Design goes much further than this and impacts almost every area of your technology use and data processing. These examples merely demonstrate some of the ways you can engineer privacy into your processes.
The 7 Principles of Privacy by Design

There are seven principles in the concept of Privacy by Design and each one is just as important as the next. These principles are:
- Proactive not Reactive/Preventative not Remedial
- Privacy as the Default
- Privacy Embedded into Design
- Full Functionality
- End-to-End Security
- Visibility and Transparency
- Respect for User Privacy
Let's start with Principle 1: Proactive not Reactive/Preventative not Remedial.
The first principle argues that data privacy needs to come up at the beginning of the planning process. If your security practice consists of putting out fires and dealing with breaches, then you are being reactive. It sets up the philosophical heart of the rest of the principles.
Principle 2 Privacy as the Default Setting is perhaps the most difficult principle for companies to wrap their minds around. It argues that privacy needs to be at the forefront of what you do. That means restricting your sharing, using data minimization, deleting data you no longer use, and always operating on a legal basis. It also means using opt-in and opt-out functions and safeguards for consumer data.
In Principle 3, the idea is that privacy needs to find a home in the design or both your architecture and business. In other words, privacy is a core functionality of the product. You should be using encryption, authentication, and testing vulnerabilities on a regular basis. It doesn't matter if your process works as it should; it has a design flaw if there's a security vulnerability.
Principle 4 puts forth that there's no reason to be afraid of Privacy by Design. If you are sacrificing functionality for privacy, then you are doing it wrong. It's more of a culture shift that requires a balance between growth and security.
Within the End-to-End Security principle (#5), there's an argument that privacy protection follows data through the lifecycle from collection to deletion/archival. Encryption and authentication are the standard at every stage, but you need to go further at other stages. For example, you should only collect data you need and have a legal basis for. And when you finish with the data, you should use GDPR-compliant deletion/destruction methods for end-to-end protection.
In the penultimate Principle 6 Visibility and Transparency, you learn that privacy isn't just for privacy's sake. Data subjects should know about your privacy (and processing) practices and you should share them in the open. The principle argues a case for a well-written Privacy Policy, which is essential if you fall under the jurisdiction of the GDPR or another law like CalOPPA, anyway. It also argues that there needs to be a mechanism for data subjects to air their grievances, ask questions, and ask for changes.
Finally, Principle 7 argues that everything needs to remain user-centric. It means acknowledging that even if you have the data, it belongs to the consumer you collected it from. Your data subject can grant and withdraw their consent for your use of their data - not the other way around.
Privacy by Design: Who's It For?

Privacy by Design is for everyone, but it's particularly important for your business if you are a data controller who falls under the scope of the GDPR.
The GDPR embraces and namechecks Privacy by Design in Article 25. However, the legislation doesn't name the exact measures to be taken beyond features like pseudonymization or encryption and anonymization. Instead, the GDPR wants privacy features to be reasonable and appropriate to both the processes you use and the data you collect.
Article 25(2) explicitly says:
"The controller should implement appropriate technical and organizational measures for ensuring that, by default, only personal data which are necessary for each specific purpose of the processing are processed."
Article 25 then refers to Article 42 and the describes the certification measures for further clarity on compliance.
Upon publication, the GDPR didn't include clarity on what the certification measures would be and who the certifying bodies are. In February 2019, the European Commission published the study on Articles 42 and 43 (certification bodies). You can read the full report here.
What if the GDPR Doesn't Apply to My Business?
Even if you won't or don't have to comply with the GDPR, Privacy by Design is still a good idea for your business.
Implementing Privacy by Design reflects an understanding of the value of personal information both to your business and to your customers. It acknowledges that privacy and personal control over data is an important freedom, and it's one that law not only increasingly reflects but also that you need to uphold on your own within the market.
If you think people aren't that worried about consumer privacy think again. A poll performed by ExpressVPN found that 71 percent of people had concerns about the ways marketers collect and use their data.
And 68 percent of American internet users said they would support a GDPR-like regulation in the United States.
Approaching privacy from a design-thinking perspective ensures it is integral to your operations from planning through to execution. It enables you to futureproof your business from both a customer and regulatory perspective.
How to Implement Privacy by Design: Article 25 Checklists

Article 25 is notoriously vague, but thoroughness is still important both for protection from threats and from GDPR fines. Whether you run a website, app or SaaS product, Privacy by Design needs to occur:
- At the design stage
- Throughout its lifecycle
- Between end-to-end engagement
- After engagement
- After your site/app comes down
The GDPR asks for "technical and organizational measures" like encryption and pseudonymization, but that's not the start and end of Privacy by Design. Unfortunately, the GDPR itself doesn't provide a checklist. You need to ask your own questions and provide your own answers with little direction from the law or its recitals.
One helpful way to break down Privacy by Design implementation is to follow it in three chunks: systems, processes, and risk management.
Systems Checklist

Privacy by Design starts with the systems in place. Because it starts at the top, that's where your list begins.
To incorporate privacy into your systems, you should begin with the following points (at a minimum):
- Having a documented organizational commitment to data protection standards (including into corporate culture, business practices, and business services)
- Appointing a data protection officer (DPO) if applicable, or using a data protection advisor (non-GDPR cases)
- Establishing a data protection framework (including encryption and anonymization)
- Creating and documenting a record-keeping system for processing activities
- Identifying a risk management system (including compliance management)
- Updating privacy training for employees who handle personal data (both for customers and other employees)
- Using self-assessment to audit and monitor the implementation of the documented systems above
- Establishing security measures used to avoid incidents and breaches
By following this checklist, you will be better prepared to then design your data processes.
Processes Checklist

The biggest focus of your Privacy by Design and GDPR compliance work happens in the processes section, but it doesn't work without first starting in your systems.
Items on your list include:
- Allocating gatekeeping responsibilities (IT, legal, procurement, etc.)
- Identifying privacy risks throughout your processes
- Documenting your data processing (using the record keeping system designed in Systems Checklist)
- Using DPIAs, risk, and compliance assessments before collecting data for use or storage
- Adding privacy controls, such as a Privacy Center, that allow data subjects access to their personal data on their terms
- Implementing the measures of the Systems checklist above
Risk Management Checklist

Even if you build privacy into your process design, you still need to manage risks throughout the data lifecycle. Risk management starts at the systems level and carries on into the processing.
You should be able to:
- Describe the purpose of the processing (legal basis)
- Identify measures that prevent data from being processed for purposes other than above
- Monitor data minimization measures and implement appropriate controls (further minimization, anonymization, and pseudonymization)
- Identify measures used for ensuring data accuracy
- Name and document the people and teams with access to the data
- Outline controls for access to data
- Create Data Processing Agreements (DPAs) and review them with each third-party processor
- Monitor implemented security practices
- Identify source of information and notice to data subjects about data processing
- Outline the process followed in the event of security and data breaches (following GDPR notification rules)
- Implement the measures of both the Systems and Processes checklists above
Remember the principles of Article 25 of the GDPR when applying the checklists.
Article 25(1) includes the following obligations and limitations to take into account:
- State of the art (remember that this changes)
- Cost of implementation
- Nature, scope, context and purposes of processing
- Risks of varying likelihood and severity for rights and freedoms of natural persons
- Appropriate technical and organizational measures
All of these contribute to best practice for Privacy by Design without making it unreachable for SMEs and those who don't take part in processing activities that come with significant risk.
In other words, you don't need to spend millions on a security system to collect only email addresses and send out a newsletter. Your practice should be appropriate to the nature, scope, context, purposes, and risks of sending out a newsletter. If you're Deutschebank, then it's a different story.
Privacy by Design is a Best Practice

Whether or not you need to comply with the GDPR, Privacy by Design is now considered to be a best practice for all organizations that engage in data processing, no matter how big or small.
Privacy by Design means considering privacy from the beginning of a project and integrating it into your systems and operations. It is not a security practice or tool to be added on later. Getting it right means encouraging an organizational culture dedicated to acknowledging and respecting the value of personal data both to your company and to your customers.
The checklists above will help you implement Privacy by Design at your company. But remember that the GDPR also wants you to consider issues like the cost of implementation, the nature and scope of the processing, and the risks that face your customers if there's a breach.
Under the GDPR, Privacy by Design is attainable for all businesses, so there's no excuse not to get started.


