Biometrics Laws and Privacy Policies

Biometrics is the latest trend in cybersecurity for both personal devices and entire networks.
In fact, around 62% of organizations are already using biometric technology as a means of authentication for their networks. That number is growing. Another 24% plan to set up their own biometric system over the next two years.
So, what are biometrics? Let's start with the word itself.
"Bio" refers to biology. In this case, it refers to biological markers or indicators.
"Metrics" refers to a system of measurement.
The term itself was cooped from the study of biometry, which is the study of biological observations. If you were to ask Biometrics Research Group, Inc., one of the companies leading the way in technology, you'd receive the following definition:
"...measurable physical and behavioral characteristics that enable the establishment and verification of an individual's identity."
Biometric characteristics range from fingerprints to iris scanners to facial recognition. While these are the most commonly applied physical characteristics in the consumer market, there are other applications available that focus on behaviors.
Scientist and security analysts are able to study these behaviors and identify unique patterns in them.
Some of the most common behaviors studied include:
- Voice recognition
- Keystroke dynamics
- Gait analysis
- Signature analysis
- Cognitive biometrics
- Mouse use characteristics
Note that a password is not a biometric behavior. While they may be unique, they only require software to set up - not hardware. Additionally, anyone can guess your password and use it to log into your account.
When you secure an account with biometric indicators, only the person who secured it can unlock it because biometric systems use a combination of hardware and software to identify the person.
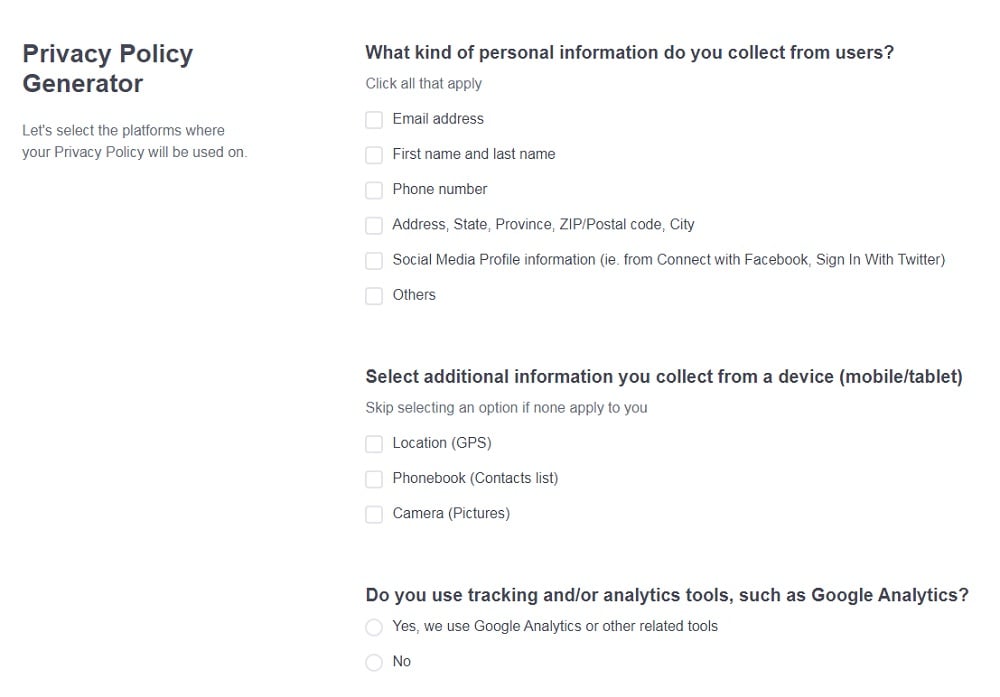
Need a Privacy Policy? Our Privacy Policy Generator will help you create a custom policy that you can use on your website and mobile app. Just follow these few easy steps:
- Click on "Start creating your Privacy Policy" on our website.
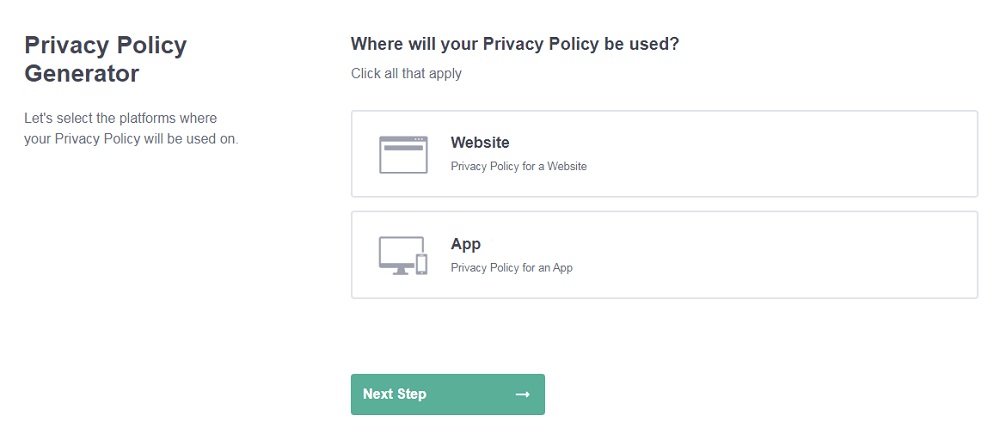
- Select the platforms where your Privacy Policy will be used and go to the next step.
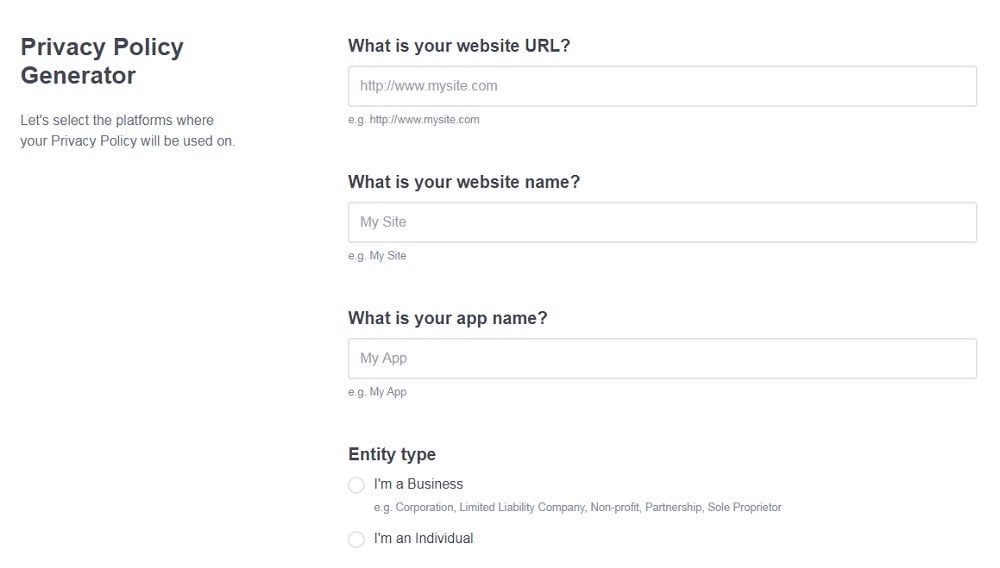
- Add information about your business: your website and/or app.
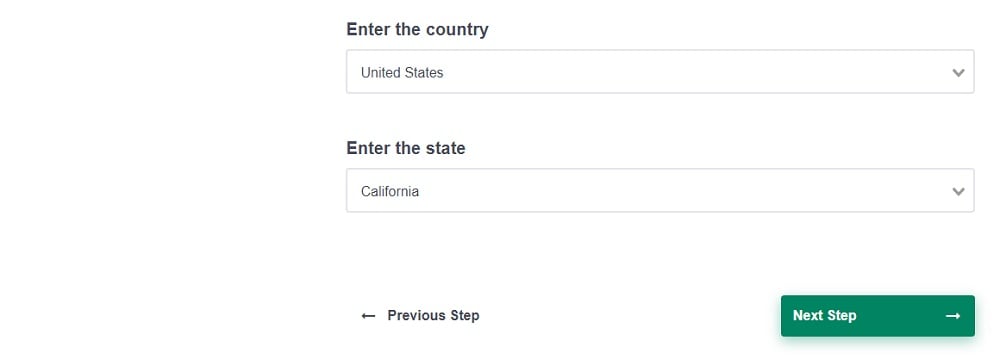
- Select the country:
- Answer the questions from our wizard relating to what type of information you collect from your users.
-
Enter your email address where you'd like your Privacy Policy sent and click "Generate".
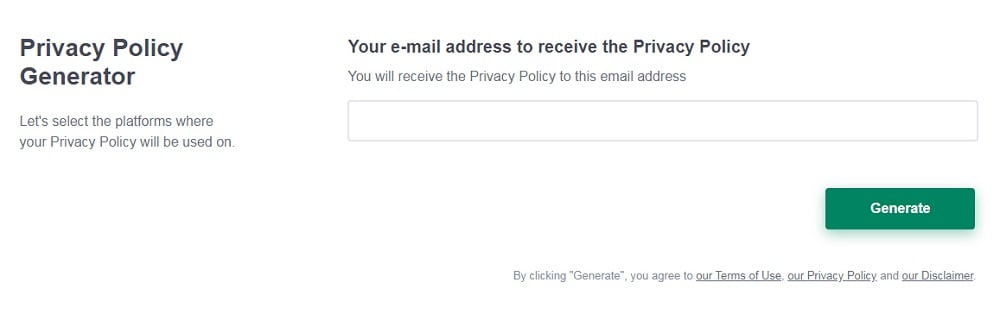
And you're done! Now you can copy or link to your hosted Privacy Policy.
- 1. How Developers are Using Biometrics
- 2. Passwords Aren't Obsolete
- 3. Laws Regulating Biometrics Use
- 3.1. Illinois Biometric Information Privacy Act
- 3.2. Texas Business and Commerce Code - BUS & COM 503.001 Capture or Use of Biometric Identifier
- 3.3. Washington House Bill 1493 (2017)
- 4. How to Comply with Biometrics Laws
- 4.1. Start With Consent
- 5. Examples of Privacy Policies That Address Biometrics
- 5.1. EmployBridge
- 5.2. Firstsource
- 5.3. Keyo
- 6. Conclusion
How Developers are Using Biometrics
Biometrics have an application throughout tech engineering and development. The science is presently being used to do some pretty cool things including predicting the quality of a developer's code by reading their heart rates. However, their current primary use is in security and authentication.
The example you're likely most familiar with is the Face ID software now available on the iPhone X.

The iPhone X allows users to unlock their phones with infrared and visible light scans able to detect the unique features in your face. It works in most lighting scenarios and promises a new level of security.
A common misconception suggests biometrics are replacing the traditional passwords, but this isn't the case. Instead, its used to supplement passwords or work as an alternative solution for two-factor authentication.
Macworld describes the capabilities of the tech best:
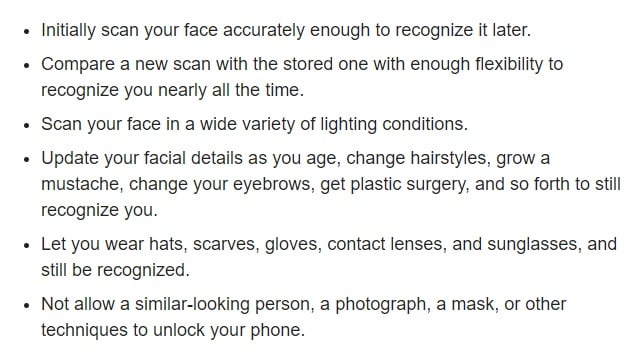
Biometrics work differently to traditional two-factor authentication because other factors like security questions, text messages, or email confirmation can be saved into the keychain and passed off as a password.
Biometric information works the same way. It offers only a pass or fail method of logging in, but it does trigger the password to be sent from the keychain to the app.
The benefit of using biometric information is that it's never stored as a password. Yet, it doesn't up the security ante either. Rather, it's a method of convenience that allows for faster logins.
Despite Apple's aggressive marketing, you can hack biometrics. Wired attempted to fool the system using the most straightforward methods, and other hackers have only been successfully using impractical techniques like 3-D printing a mask of the phone owner's face.
However, a 10 year old kid recently hacked into his mother's iPhone X. His face offered enough facial similarities that the phone unlocked immediately when he picked it up. Apple has even admitted that non-identical family members may be able to get into their relative's phones.
Passwords Aren't Obsolete
Because biometrics don't add as much security as they appear to, developers will continue to rely on username and password security for the near future.
Passwords aren't going away.
Nor should they.
Unlike biometric information, passwords are changeable in the event of a cyber attack. Additionally, passwords remain essential in a physical attack on your accounts. Your password doesn't exist anywhere outside of your brain, so if you have a strong password, you're better protected than if you find yourself in a hostage situation. You can't change your fingerprint, which leaves you nearly eternally vulnerable if an attacker is successful.
Passwords are personal, but they're ultimately changeable and are meaningless without a username.
Biometric information, however, is intimate. It's personal in a way the most embarrassing screen names and passwords could never be. You can't change your face or fingerprints enough to overcome a hack of your biometric information - not at least, without some sort of underworld surgical operation and a serious amount of money.
The best solution for security remains a strong password left on a zero knowledge product.
Laws Regulating Biometrics Use

Because biometrics are the most personal of personally identifiable information, state laws now regulate it.
There are three states with laws to look out for:
- Illinois
- Texas
- Washington
Illinois Biometric Information Privacy Act
Illinois passed a specific biometric privacy law before any other state. It's the archetype of biometric privacy laws that other states - Texas and Washington - would draw up on later.
The Illinois Biometric Information Privacy Act (BIPA) refers to biometric data as the following:
- Retina scan
- Iris scan
- Fingerprint
- Voiceprint
- Hand scan
- Face geometry
It doesn't include things like demographic data, physical descriptions, writing samples or photographs.
The law is long and sweeping, with five main requirements.
- Businesses must achieve informed consent before collecting biometric data.
- Businesses have limited rights for disclosure.
- Businesses may not profit from biometric data.
- Businesses must protect and retain the data according to the statute.
- Individuals harmed by a violation of the law may receive $1,000 per negligent violation or $5,000 per intentional violation through a private right of action.
Illinois passed BIPA in 2008, but it meant little until five class action lawsuits were filed in 2015 against businesses that had violated the law.
Although the law has been on the books for a decade, it's continuing to evolve. If you do business and work with biometrics in Illinois, it's imperative to continue watching these changes.
As a rule, businesses find that it's prudent to collect only the necessary biometric information and retention should not continue longer than required for a specific business purpose. Businesses also need a plan for storing, protecting, and sharing biometric information. The plan should be formally enacted with the administrative, physical, and technical safeguards for caring for the data all in place.
Texas Business and Commerce Code - BUS & COM 503.001 Capture or Use of Biometric Identifier
The Texas law offers the same foundation as the Illinois law. It also includes only eye, face, finger, hand, or voice scans and relies on consent prior to the collection of the biometric data.
This law began in 2009 and requires businesses to:
- Refrain from selling, lease or disclosing biometric information without consent
- Store and protect identifying information from disclosure
- Destroy the information no later than the first anniversary of the date the information was collected unless otherwise specified
The law applies to anyone who use the identifiers for "commercial purposes" but the law does not extrapolate on what it means by "commercial purposes."
Washington House Bill 1493 (2017)
Wasthington's biometrics law was signed into effect on May 16, 2017. It applies to individuals and non-government entities (businesses) and regulates the way those parties are able to collect, store, and use biometric identifiers.
Anyone in Washington is prohibited from "enrolling a biometric identifier in a database for a commercial purpose, without first providing notice, obtaining consent, or providing a mechanism to prevent the subsequent use of a biometric identifier for a commercial purpose."
Washington's law is similar to both the archetypal law in Illinois and the later law in Texas in the way it regulates collecting, using, and retaining data. The primary difference is that Washington does not offer a private right of action in its law. Illinois does offer this remedy but Texas does not.
How to Comply with Biometrics Laws

If you do business in Illinois, Texas or Washington, (note that New York has some regulation in progress at the time of this article being published), you need to comply with these laws or risk serious fines for every infraction.
Most of the laws apply only to businesses or individuals, but some laws do not specifically state which uses fall under the jurisdiction of the law.
The way you choose to manage, store, and destroy the biometric data you collect is up to you. As long as you are compliant and ensure the information is not sold or leaked, then you're free to choose which services to engage to uphold your end of the bargain.
Start With Consent
Compliance with the laws lies first in receiving consent from the owner of the data before collecting it.
There are two things you need to do here.
First, you should update your Privacy Policy to include information about your collection, storage, and use of biometric information. A special section of your Privacy Policy should reflect your obligations when dealing with biometric data, including informing visitors that you'll be collecting this data.
The second thing you need to do is use clickwrap to require your website visitors or app users take some sort of affirmative step to show they're giving their consent for you to use their biometric information.
Something like a checkbox or I Agree button works well to get clear, affirmative consent.
Examples of Privacy Policies That Address Biometrics
Biometric data is used in healthcare, HR, and across tech generally. We've provided two HR examples and a general consumer business example of biometric Privacy Policies.
EmployBridge
EmployBridge created a dedicated Biometric Information Privacy Policy to comply with the Illinois Biometric Information Privacy Act:

It includes the following sections and clauses:
- Definition of "biometric identifier" and "biometric information"
- Consent
- Disclosure
- Storage
- Retention Schedule
Within the Consent clause, the company states that all employees are handed a physical consent form to read and sign prior to handing over any biometric details. All Illinois employees are required to sign the form.

Firstsource
Firstsource offers a Biometric Information Security Policy.
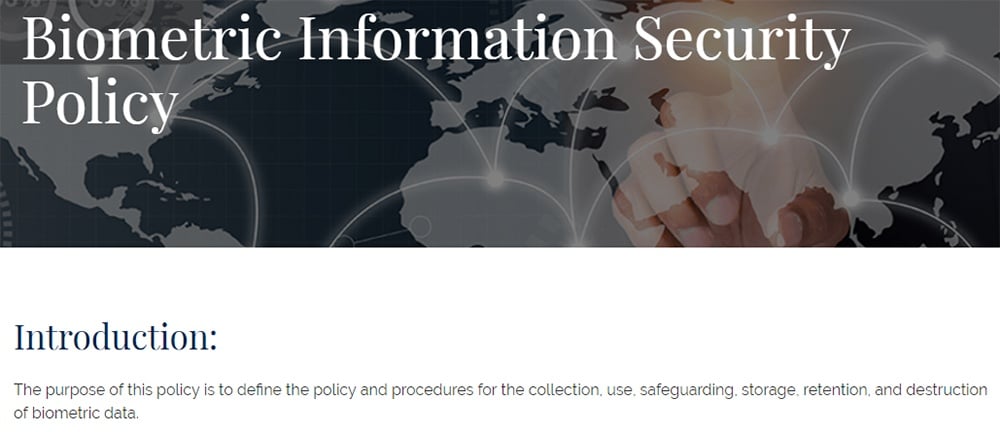
Firstsource defines biometric data and notes its own responsibilities in dealing with the data.
The Policy states what law it agrees to uphold and notes the key tenets of the law: consent, procedure, and privacy. Part of the law is dedicated to Illinois employees.
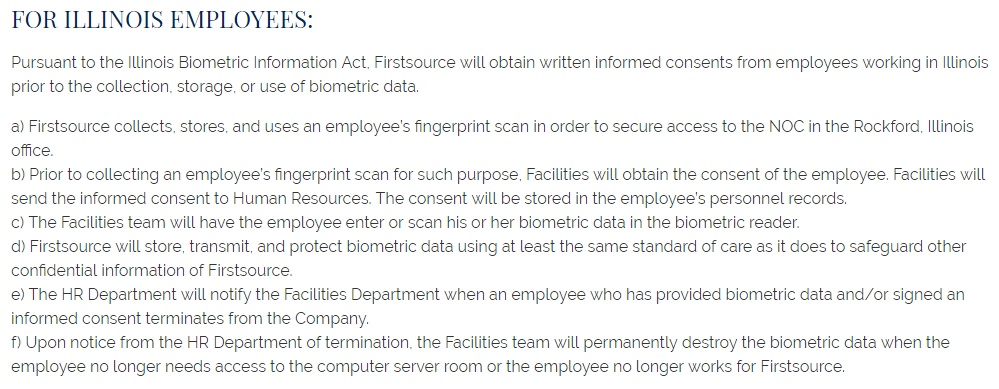
A separate section is written from employees from other states.
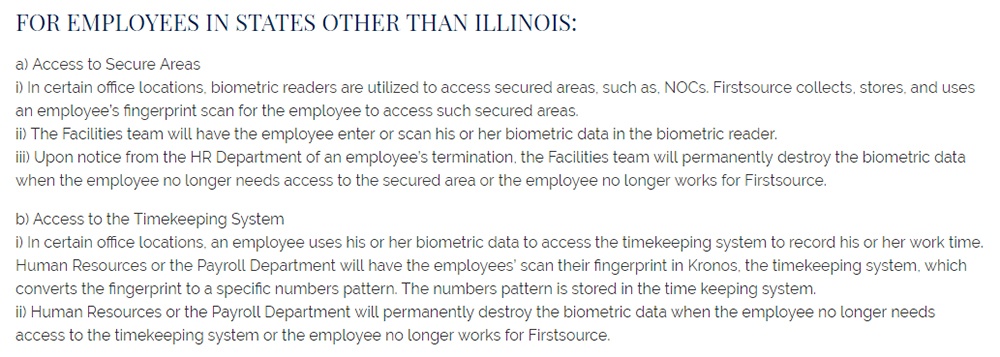
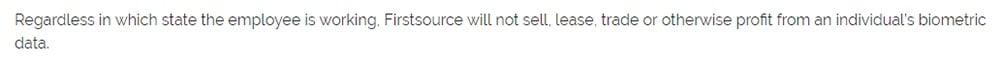
Some parts of the policy remain the same across the board:
Keyo
Finally, Keyo offers a specific Biometric Data Policy. Unlike the other two examples, Keyo isn't implemented by HR teams. It's open to anyone including businesses and customers.
Keyo is a consumer product that replaces keys, payment, and ticketing systems with biometric data - a scan of your hand. Keyo's Biometric Data Policy is structured like a FAQ, which makes it easy for general consumers to understand:
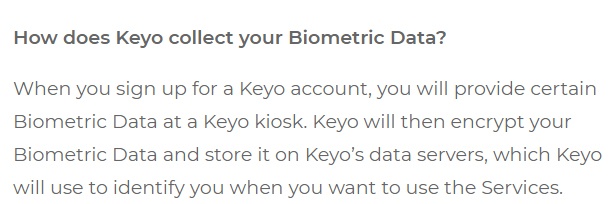
Keyo makes it clear to its customers what happens with biometric data after accounts are closed:
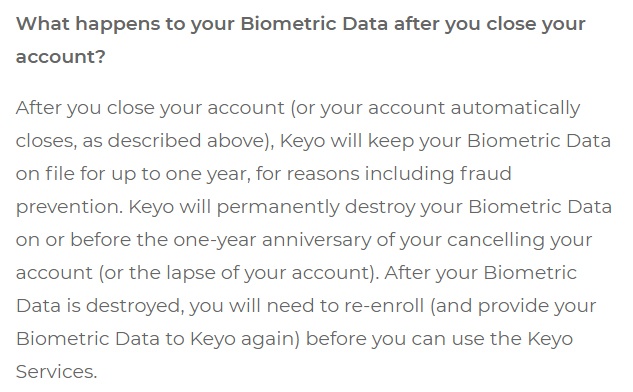
Keyo's Policy is an excellent example because it clearly describes the process of collecting, storing and deleting such sensitive data in an easy-to-follow way.
Conclusion
If you're a non-governmental organization and you work with biometric data, you're obligated to care for that data according to law. Although only Illinois, Texas, and Washington presently have laws, it's worth your while to follow the those guidelines regardless of whether you operate in those states. This is because more states are surely going to developing these laws as time goes on.
Biometric data isn't like a password. If it's compromised, it cannot be changed and has serious implications for the lives of those who own it. That's why every business should seek consent prior to collecting this type of personal data and ensure transparency in the way biometric data is collected, stored, and disposed of.
Make sure your Privacy Policy addresses this information and your use of it.


![How to Protect Your Mobile Phone Privacy [Calls, SMS & Location Data]](https://www.privacypolicies.com/public/uploads/2018/02/how-to-protect-your-mobile-phone-privacy.jpg)