Creating an IT Security Policy

An IT Security Policy is a document that sets out how people can use your IT equipment and network. It explains what steps you take to protect data, and what you expect from users in return.
In other words, an IT Security Policy tells people everything you're doing to prevent a cyber attack or data breach, and how you expect your users to help you achieve those goals.
Furthermore, an IT Security Policy establishes what happens if there's a data breach. It sets out clear instructions for people to follow, which helps people report security incidents without delay.
Are IT Security Policies legally required, or can you cover cybersecurity issues elsewhere? Let's take a look.
- 1. Why You Need an IT Security Policy
- 2. IT Security Policy Template
- 2.1. Security Objectives
- 2.2. Relevant Law
- 2.3. Scope
- 2.4. Any Key Personnel
- 2.5. Internet and Network Usage
- 2.6. Cybersecurity Best Practices
- 2.7. Antivirus Software and Protective Measures
- 2.8. Data Backups
- 2.9. Erasure and Disposal
- 2.10. Bring Your Own Device (BYOD)
- 2.11. Penalties for Not Complying
- 2.12. Data Breach Reporting
- 3. Conclusion
Why You Need an IT Security Policy
To be clear, businesses don't need an IT Security Policy under the law. However, that doesn't mean you should skip out on drafting one.
Here's why:
- A clear IT Security Policy makes it easier for everyone to understand the rules.
- If users understand the rules, there's less chance of a data breach.
- And, if there is a data breach, a written Security Policy helps you identify what procedures to follow, which minimizes disruption.
IT Security Policies are sometimes designed to be read alongside other documents, like your Privacy Policy or Data Protection Policy.
Need a Privacy Policy? Our Privacy Policy Generator will help you create a custom policy that you can use on your website and mobile app. Just follow these few easy steps:
- Click on "Start creating your Privacy Policy" on our website.
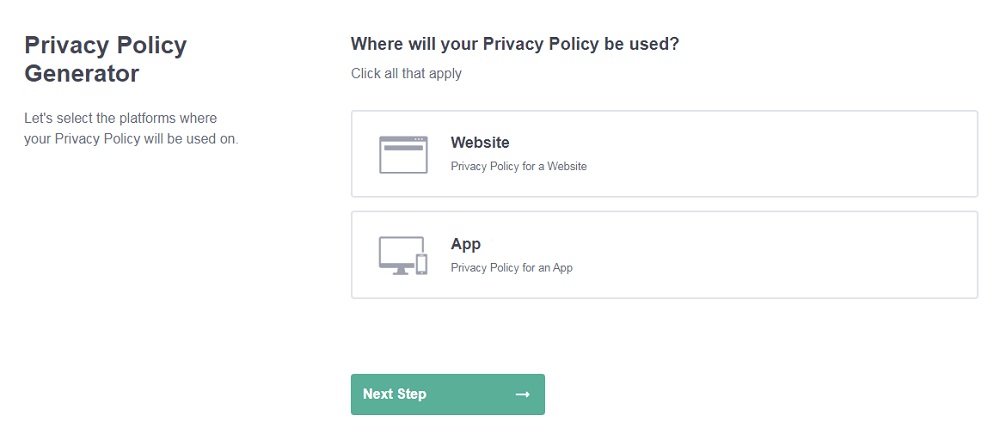
- Select the platforms where your Privacy Policy will be used and go to the next step.
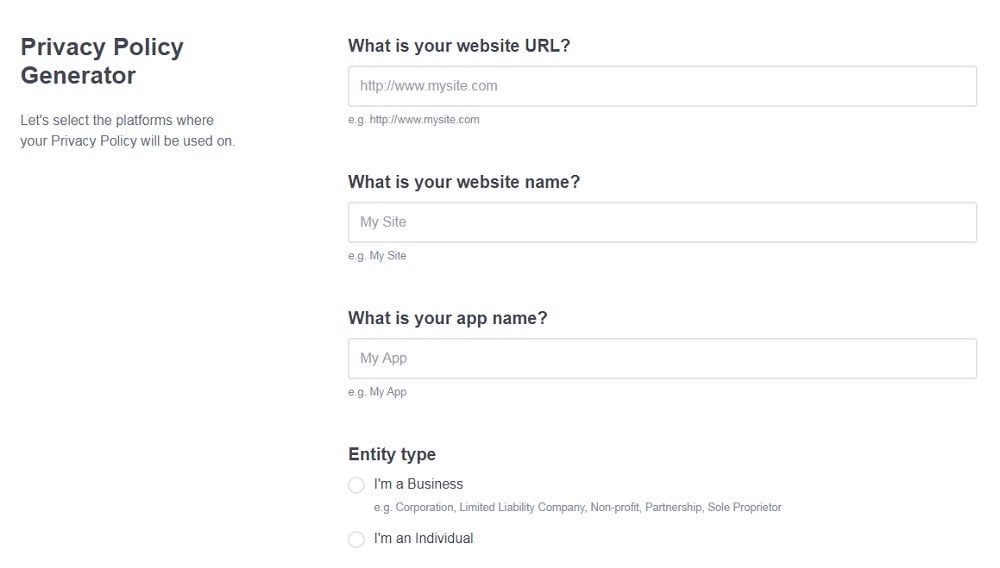
- Add information about your business: your website and/or app.
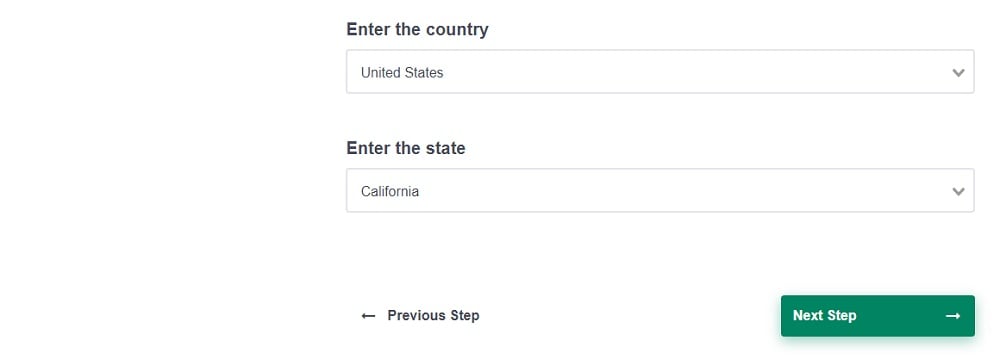
- Select the country:
- Answer the questions from our wizard relating to what type of information you collect from your users.
-
Enter your email address where you'd like your Privacy Policy sent and click "Generate".
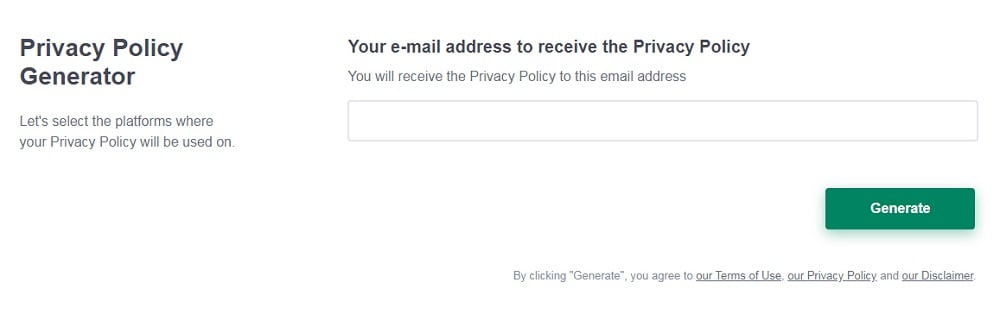
And you're done! Now you can copy or link to your hosted Privacy Policy.
Here's an example of how you might word this from Manchester Metropolitan University:

Ultimately, an IT Security Policy helps you create a culture of cybersecurity and transparency. It shows all users that you're committed to data protection, which can boost your reputation.
So while you don't need an IT Security Policy, having one comes with so many benefits that it's worth spending the time writing one.
IT Security Policy Template

Let's briefly summarize what you should include before looking at each clause in a bit more detail.
First, every IT Security Policy should have, at minimum, clauses covering the following information:
- The policy's objectives (in this case, cybersecurity)
- Who the clause applies to, and what laws apply
- The person(s) responsible for implementing the policy
- Using the internet safely
- Good cybersecurity practices, including passwords and multifactor authentication
- Hardware processes, including network security
- How you use software, and how you protect personal data
- The ways you handle data breaches and mitigate risk
- Where someone can go for more information, or how to contact you
This might seem a lot, but it's not actually as much as it looks. In fact, some IT Security Policies are just a few paragraphs long.
Here are some tips to keep in mind when you create your IT Security Policy:
- Use concise, user-friendly language
- Try to keep sentences short
- Bullet points can help get a point across
- Put everything in a logical order
- Include links to your other important documents so that people can access everything from the one location
Now let's look at specific sections and what information they should include.
Security Objectives
It sounds obvious, but you need an introduction setting out that it's an IT Security Policy and what that means.
Here's an example from NYU. From the introduction, it's clear that the Policy is about how NYU protects data shared across its network:

So you don't need a long clause. It just needs to be obvious what the Policy is about. In this case, it's security objectives.
Relevant Law
One of the benefits of having an IT Security Policy is that you can easily demonstrate that you comply with relevant laws. Which laws apply depend upon your sector and country.
In your IT Security Policy, highlight which laws you're abiding by. You don't need to list them all. It's fine to just note the most important laws.
Here's an example from the University of Huddersfield:

Scope
First, be clear about who the Policy applies to. How you draft this clause depends on who you want to include, but at a minimum, it should apply to:
- Company employees
- Contractors
- Anyone else who uses your system such as faculty members or students
Then, confirm what systems and devices fall under the scope of the IT Security Policy. In most cases, you'll want to include personal and company-owned devices, but this might not always be the case.
Yale University has a nice and simple clause for this. It's clear the policy covers everyone who access the university system, no matter what device they use:

Any Key Personnel
Make sure people know who is in charge of implementing your IT Security Policy. If there are multiple employees or departments involved, you should explain what different roles they play. The point is so that people know who to contact if they have any questions about how your policy works.
Harvard University, for example, has one point of contact - the Chief Information Security Officer. There's an email address included for people to contact the individual if they have any IT Security questions:

Internet and Network Usage
Ideally, you should establish what sites people can access what they can download while using your network. Tell people that you monitor their internet usage and specify what kind of behavior isn't acceptable.
Here's an example from the University of Huddersfield. First, it confirms that it routinely monitors internet usage:

Then it sets out some examples of unacceptable internet use:

Cybersecurity Best Practices
Encourage good security practices while people use your IT. For example, this might include:
- Keeping passwords private
- Using 2-step authentication
- Ensuring no one else uses their login details
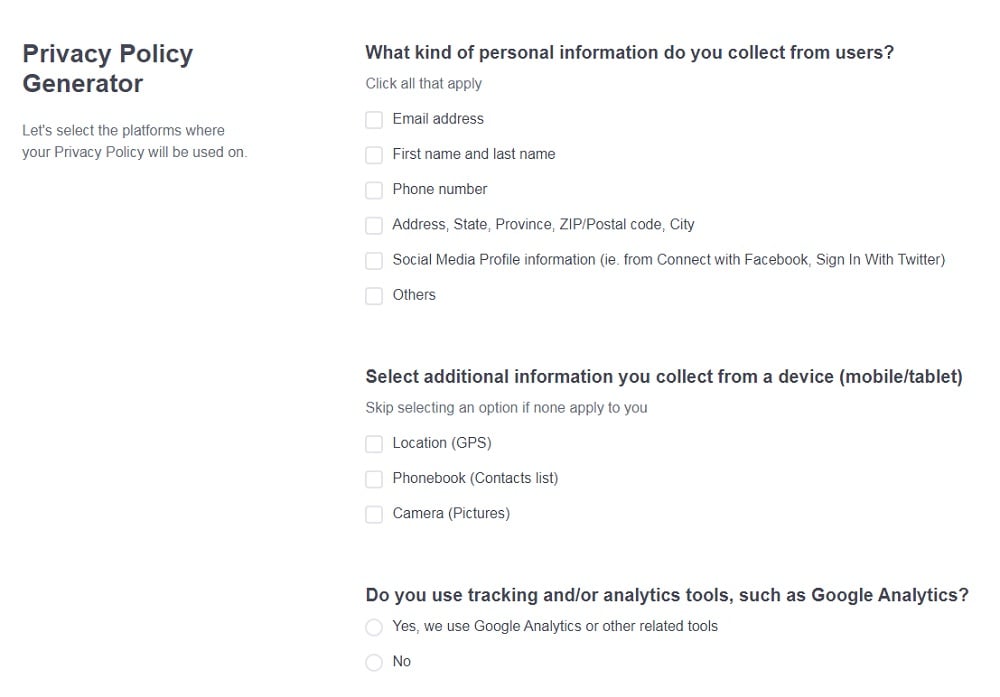
- Trying to access data they aren't authorized to see
Remember, the goal is to create a safety-conscious, responsible IT culture.
Here's an example of some good practices set out by the University of Glasgow in its IT Services Policy:
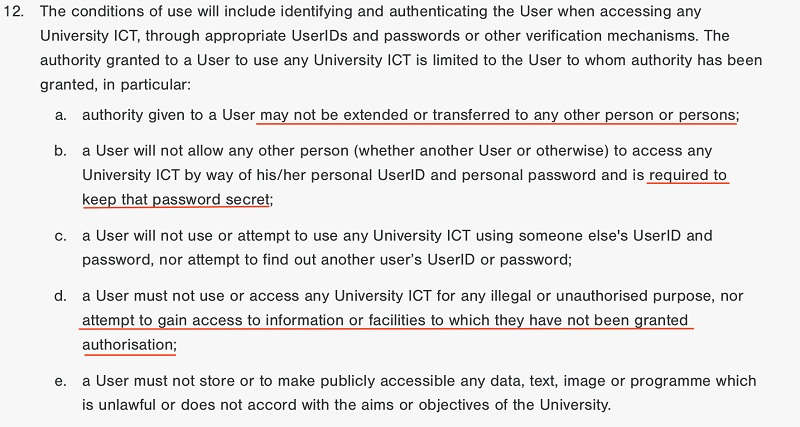
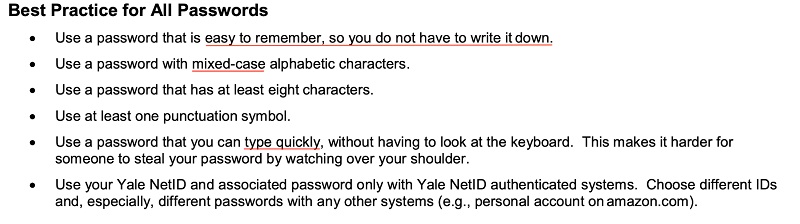
Yale sets out specific guidance for creating strong passwords, because this is one of the best ways for users to keep their accounts and data safe:
Antivirus Software and Protective Measures
You should always ensure systems are protected with up-to-date antimalware and antivirus software. It's a good idea to emphasise this in your IT Security Policy.
But don't forget to set software rules for users, too. For example, if you give users a temporary license to use software, they should only use it for a set purpose, and they shouldn't infringe your intellectual property rights.
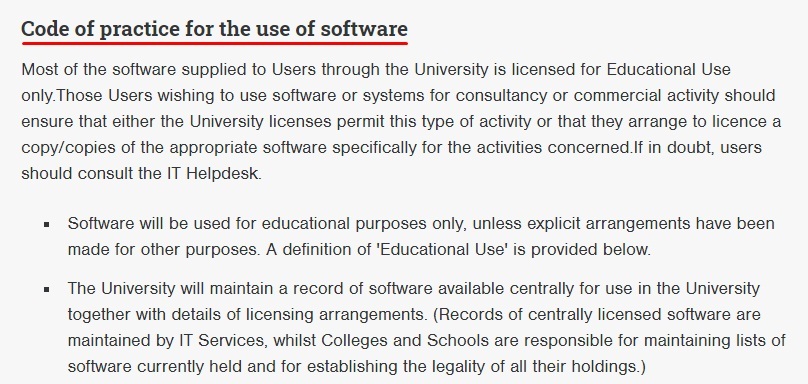
The University of Glasgow sets clear software security protocols for its users. People can only use software for educational use or some other defined purpose, and they can't copy it or distribute it:
Data Backups
Offer guidance for how users can safely back up data, and encourage them to do so frequently. Otherwise, you risk irreversible data loss which could damage your business.
The University of Huddersfield has a simple but effective clause for this. Key personnel must ensure there's sufficient backup processes in place, and data recovery is a business priority. There's also emphasis on ensuring personnel use safe restoration processes:
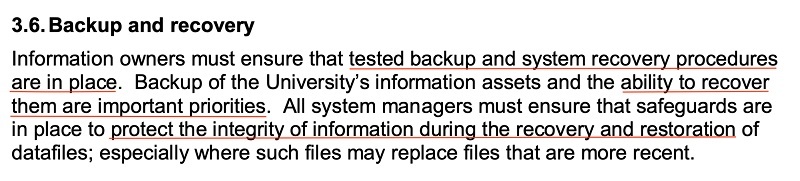
Erasure and Disposal
Set clear rules for how people can safely dispose of IT equipment or confidential data once it's no longer needed. Here's an example of such a clause from the University of Huddersfield:

You could set similar rules for procuring or buying new hardware, or installing new network infrastructure. Everything must be done securely to a set company standard.
Bring Your Own Device (BYOD)
If you let people access your network from their own device, or if they can work from home, you need to set some security guidelines. These guidelines might include:
- Using firewalls
- Setting up encryption
- Always using secure networks
- Never leaving devices unattended
- Reporting accidental theft, damage, or other potential security incidents
At the University of Huddersfield, you need authorization to work remotely:
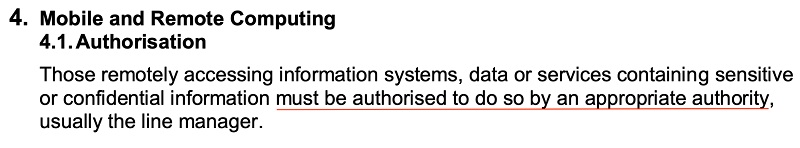
And students should not access university IT or do work off-campus unless they have proper safeguards in place:

Finally, users must be responsible and take steps to avoid loss or damage, especially when travelling or moving around off-campus.
This is a good clause because there's contingency planning. Even if the device is lost, unauthorized people can't access the content if users ensure there's encryption or other security measures in place:

Again, the emphasis is always on ensuring sensitive data stays safe and protected, no matter where staff or students are located. This is an especially important point for offices where remote working is commonplace.
Penalties for Not Complying
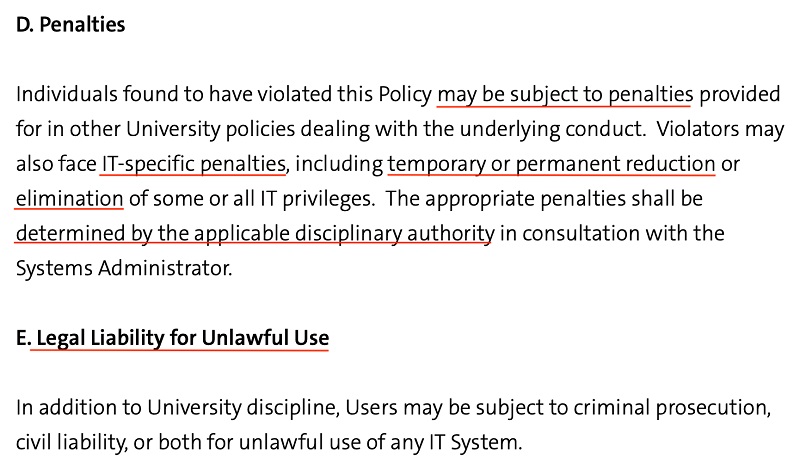
Always include what repercussions will be for someone who doesn't follow your policy. This can be things like temporary or permanent revocation of access, loss of use of company devices and other penalties.
Here's a penalty clause from Yale, as well as one that addresses liability issues:
Data Breach Reporting
It's vital that you explain what you expect people to do if there's a data breach, and how you plan on notifying affected users. Some laws impose mandatory reporting requirements.
The key here is making sure you know what rules apply to your business, and communicating them in your IT Security Policy.
The University of Queensland has some great clauses addressing the data breach issue. First, there's a clause confirming its mandatory reporting obligations:

The University also sets out who is responsible for reporting incidents, and when:

Conclusion
Although a formal IT Security Policy isn't legally required in most cases, it's an easy way to comply with your data protection obligations under relevant laws, while helping keep your IT environment more secure.
Your IT Policy should include, at minimum, the following details:
- An introduction stating your policy objectives
- The scope, or who is covered by the policy
- The laws governing the policy
- Contact information for key personnel
- Advice on permitted internet usage
- Hardware and software requirements
- Rules for remote working
- BYOD advice
- Details on how you handle and report data breaches
Without an IT Security Policy, it's much harder to ensure your users browse the web or use your network safely.


